I attended the RSA Conference USA last week and was able to witness the chaos, FUD, genuine insight, original thoughts and 25,000 people queueing for a coffee and bagel at 10 o’clock in the morning.
I attended the RSA Conference USA last week and was able to witness the chaos, FUD, genuine insight, original thoughts and 25,000 people queueing for a coffee and bagel at 10 o’clock in the morning.
Rather than even attempt to do an end of show round up that other have been able to do far more successfully than me, here are the five things that I remembered the most from the week:
3M Visual Privacy
I still think 3M produce the best privacy filters for monitors, but I have been waiting a long time for technology to catch up and remove the unsightly and easily-left-behind at home piece of plastic in favour of a solution built into the screen itself. Whilst I didn’t unfortunately see that, one of the product managers assured me that this is exactly what the boffins at 3M are currently working on. This is going to be a huge step towards universal and transparent (forgive me) visual security for people using laptops in public places.
 3M also surprised me by demonstrating a pice of software they have designed as well; the known problem with privacy filters is that they only protect you from people looking at your screen from your left or right. From directly behind you they can easily see your screen. The software uses the built in webcam to recognise the users face, and if another face appears in the background looking at the screen, pops up a warning to the user and blurs the screen. To be honest it was a little clunky when I saw it, and it is currently only being developed for Windows, but this is exactly the sort of environment that people working with sensitive information need to “watch their backs” almost literally. I hope they continue to refine the software and expound it to all other major platforms.
3M also surprised me by demonstrating a pice of software they have designed as well; the known problem with privacy filters is that they only protect you from people looking at your screen from your left or right. From directly behind you they can easily see your screen. The software uses the built in webcam to recognise the users face, and if another face appears in the background looking at the screen, pops up a warning to the user and blurs the screen. To be honest it was a little clunky when I saw it, and it is currently only being developed for Windows, but this is exactly the sort of environment that people working with sensitive information need to “watch their backs” almost literally. I hope they continue to refine the software and expound it to all other major platforms.
Security Bloggers Meetup
 RSAC USA sees the annual meet up of the Security Bloggers Network, so i was very excited to be able to attend this year and witness the awards show and a great deal of silliness and nonsense (to whit, the “bald men of InfoSec” picture for one). I managed to meet for the first time a whole bunch of people that I have either conversed with or followed myself, and some of whom I have very much admired. No name dropping I am afraid as there is too much of that later on in this post, but one thing I did take away was that there is a very valid desire to harmonise the North American and European Security Blogger Awards moving forwards which can only be a good thing and build the international blogger network further. In fact, you can now nominate for the EU Security Bloggers awards here.
RSAC USA sees the annual meet up of the Security Bloggers Network, so i was very excited to be able to attend this year and witness the awards show and a great deal of silliness and nonsense (to whit, the “bald men of InfoSec” picture for one). I managed to meet for the first time a whole bunch of people that I have either conversed with or followed myself, and some of whom I have very much admired. No name dropping I am afraid as there is too much of that later on in this post, but one thing I did take away was that there is a very valid desire to harmonise the North American and European Security Blogger Awards moving forwards which can only be a good thing and build the international blogger network further. In fact, you can now nominate for the EU Security Bloggers awards here.

The “infamous” bald men of security.
SnoopWall and Miss Teen USA
 It wouldn’t be a security conference without some kind of booth babe furore and this one was no different. Although the presence of booth babes has dramatically reduced over the last few years there were still a few vendors insisting on using them. And then we thought we had hit a new time low with the presence of Miss teen USA, Cassidy Wolf, at the SnoopWall booth in the South Hall. Condemnation was rapid and harsh. BUT WAIT… THERE’S MORE TO THIS STORY THAN MEETS THE EYE! After I retweeted my feelings about a teens presence at a conference that could best be described as a recovering alcoholic when it come misogyny, I was contacted by Patrick Rafter, the
It wouldn’t be a security conference without some kind of booth babe furore and this one was no different. Although the presence of booth babes has dramatically reduced over the last few years there were still a few vendors insisting on using them. And then we thought we had hit a new time low with the presence of Miss teen USA, Cassidy Wolf, at the SnoopWall booth in the South Hall. Condemnation was rapid and harsh. BUT WAIT… THERE’S MORE TO THIS STORY THAN MEETS THE EYE! After I retweeted my feelings about a teens presence at a conference that could best be described as a recovering alcoholic when it come misogyny, I was contacted by Patrick Rafter, the owner VP of Marketing of SnoopWall.
They have partnered with Cassidy to promote privacy amongst teens in complement to their product that detects the misuse of, for instance, the webcam on your computer or your phone. For those that may not know, Cassidy was the victim of blackmail from an ex classmate who hacked into her webcam in her bedroom, took photos and then demanded more pictures. It goes without saying she stood up to the blackmailer, and has since made privacy one of her “causes” during her tenure as Miss Teen USA. Was having her at their booth at RSA a little misjudged? Yes. Is their cause and campaign (and software for that matter) actually have very good intentions? Absolutely. I chatted with Patrick a day later and while he acknowledged how Cassidy’s presence could have been misinterpreted, he strongly defended her presence and her intentions. I honestly found it laudable. Hopefully over the next few years as the industry finally sorts out its booth babe problem, people like me won’t be jumping to the wrong conclusions as we assume the worst.
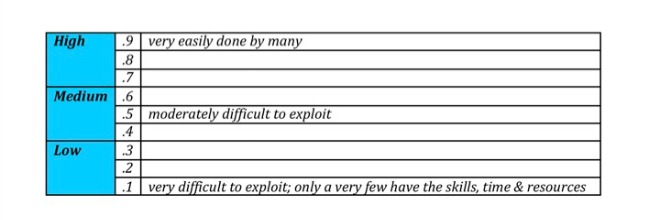
The Thomas Scoring System
 A few months ago I posted about Russell Thomas’ approach to risk management. I had the good fortune to meet with Russell at the Security Bloggers Meet Up and chatted in depth about his approach to measuring risk consistently. He has turned this idea into a very practical approach via an Excel spreadsheet, a point I made in my earlier review. This is important because without a way to implement at a very practical level it remains a theory. The following day Russell was kind enough to walk me through how to use the system in practical terms, and I am going to be trying it out in my day job as soon as possible. I would urge you to take a look at the Thomas Scoring System as I strongly believe it is a great way of bringing metrics together in a meaningful way.
A few months ago I posted about Russell Thomas’ approach to risk management. I had the good fortune to meet with Russell at the Security Bloggers Meet Up and chatted in depth about his approach to measuring risk consistently. He has turned this idea into a very practical approach via an Excel spreadsheet, a point I made in my earlier review. This is important because without a way to implement at a very practical level it remains a theory. The following day Russell was kind enough to walk me through how to use the system in practical terms, and I am going to be trying it out in my day job as soon as possible. I would urge you to take a look at the Thomas Scoring System as I strongly believe it is a great way of bringing metrics together in a meaningful way.
Gene Kim & The Phoenix Project
I was fortunate enough to have been introduced to Gene Kim, the founder of Tripwire, author, DevOps enthusiast and all round genius/nice guy a few months ago, and we had chatted a couple of times over Skype. (Gene is very generously offering me his guidance around writing a book and his experiences publishing it; yes you heard it here first folks, I intend to write a book!) Knowing he was at RSA I was able to seek him out, and I can now say I have met one of my InfoSec heroes. He is a genuinely charming, funny and generous guy, and he was good enough to sign a copy of his book, The Phoenix project, as well as allow me to get a selfie with him. I would strongly encourage everyone in this field, as well as many of those not in it to read The Phoenix Project, as it quite literally changed the way I looked at the role of InfoSec in a business, and that wasn’t even the main thrust of the book.

Gene very graciously allowing me to take a selfie with him
It has taken me nearly a week to recover from RSA, but despite the scandal and boycotts and minor demonstrations it was an excellent conference, as much for the presentations as the “hallway track”. As always, my thanks to Javvad for being my conference wing man again.

Is that Javvad, or a waxwork I am posing with?
Now it is back to real life.
 I think David was right to ask the question because it has uncovered with greater clarity something that I and many other have been talking about for some time now, namely that security for too long has been carying out secrurity for its own sake rather than supporting the business achieve its goals. In my own paraphrased words “this is what I need security to do to help me sell more beer“.
I think David was right to ask the question because it has uncovered with greater clarity something that I and many other have been talking about for some time now, namely that security for too long has been carying out secrurity for its own sake rather than supporting the business achieve its goals. In my own paraphrased words “this is what I need security to do to help me sell more beer“.